Windows Defender Features
Microsoft Defender for Endpoint is an enterprise endpoint security platform designed to help enterprises prevent, detect, investigate, and respond to advanced threats on their endpoints. Endpoints include laptops, phones, tablets, PCs, access points, routers, and firewalls.
Operating systems
Defender for Endpoint supports the following operating systems:
- Windows
- macOS
- Linux
- Android
- iOS
Defender for Endpoint capabilities
This section lists key Defender for Endpoint capabilities and provides links to more detailed information.
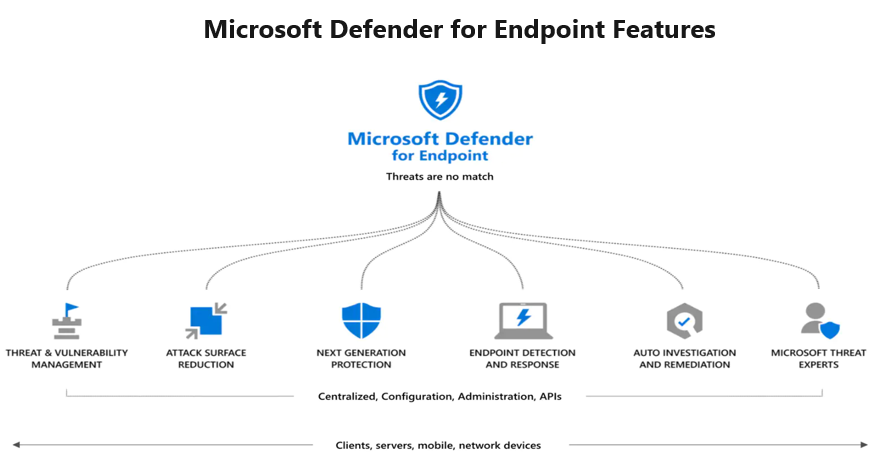
Threat and Vulnerability Management
1. Core vulnerability management capabilities use a modern risk-based approach to the discovery, assessment, prioritization, and remediation of endpoint vulnerabilities and misconfigurations.
Defender Vulnerability Management, you can empower your security and IT teams to bridge workflow gaps and prioritize and address critical vulnerabilities and misconfigurations across your organization.
Attack Surface Reduction
The attack surface reduction set of capabilities provides the first line of defense in the stack. By ensuring configuration settings are properly set and exploit mitigation techniques are applied, the capabilities resist attacks and exploitation.
This set of capabilities also includes network protection and web protection, which regulate access to malicious IP addresses, domains, and URLs.
ASR rules target certain software behaviors, such as:
- Launching executable files and scripts that attempt to download or run files
- Running obfuscated or otherwise suspicious scripts
- Behaviors that apps don’t usually occur during normal day-to-day work
Next Generation Protection
Microsoft Defender for Endpoint includes next-generation protection to reinforce the security perimeter of your network.
Next-generation protection was designed to catch all types of emerging threats. In addition to Microsoft Defender Antivirus, your next-generation protection services include the following capabilities:
Behavior-based, heuristic, and real-time antivirus protection,
Cloud-delivered protection.
Dedicated protection and product updates.
Endpoint Detection and Response.
Endpoint detection and response capabilities in Defender for Endpoint provide advanced attack detections that are near real-time and actionable.
Security analysts can prioritize alerts effectively, gain visibility into the full scope of a breach, and take response actions to remediate threats.
When a threat is detected, alerts are created in the system for an analyst to investigate.
Defender for Endpoint continuously collects behavioral cyber telemetry.
This includes process information, network activities, deep optics into the kernel and memory manager, user login activities, registry and file system changes, and others.
Microsoft Threat Management
Microsoft Threat Experts is a managed threat hunting service that provides your Security Operation Centers (SOCs) with expert level monitoring and analysis to help them ensure that critical threats in your unique environments don’t get missed.
This managed threat hunting service provides expert-driven insights and data through these two capabilities:
Targeted attack notification.
Access to experts on demand.
