Custom Device Compliance Policy in Intune
With the Custom Device Compliance, you can able to create a create your own compliance. Below are the benefits for Custom device Compliance.
- With the Intune help you can protect organizational data by requiring users and Device data with meet some requirements that’s called compliance policy.
- In Intune we can set rules and settings that user and device must meet to be an compliant.
- We can include actions on noncompliant device, User can alert if device is noncompliant.
- It can be combined with the Conditional access to block user or device if not compliant.
- Can override the configuration of settings that you also manage through device configuration policies.
Before you start, be ready with the PowerShell and Jason File.
You can download PowerShell from below link
https://github.com/harvansh007/Intune-Custom-Device-Compliance/blob/main/Intune%20Compliance.PS1
$Defender = Get-MpComputerStatus | Select-Object AMServiceEnabled,AMServiceVersion, AntivirusSignatureAge
#===================== Defender Enable Status =============================================
$DefenderStatus = $Defender.AMServiceEnabled
#===================== Defender AMServiceVersion =============================================
$DefenderAMVersion = $Defender.AMServiceVersion
#===================== Defender AntivirusSignatureAge =============================================
$DefenderSigAge = $Defender.AntivirusSignatureAge
#===================== Operating System Version ======================================
$OSVerion = (Get-ComputerInfo | select OsHardwareAbstractionLayer).OsHardwareAbstractionLayer
#=================== To get Windows Defender Firewall Services =======================
$DefService = (Get-Service -Name BITS -ErrorAction SilentlyContinue).Status
if($DefService -eq "Running") {$DefServices = "$true"}
else
{$DefServices = "$false"}$has = @{ DefenderStatus = $DefenderStatus; DefenderVersion = $DefenderAMVersion; SigStatus = $DefenderSigAge; OSVersion =$OSVerion ;DefenderServiceStatus = $DefServices}
return $has | ConvertTo-Json -Compress
Now Get ready with Jason file for your PowerShell.
https://github.com/harvansh007/Intune-Custom-Device-Compliance/blob/main/Compliance%20Json.Json
{"Rules":[{“SettingName”:”DefenderStatus”,“Operator”:”IsEquals”,“DataType”:”Boolean”,“Operand”:”True”,“MoreInfoUrl”:”https://learn.microsoft.com/en-us/mem/intune/protect/device-compliance-get-started”,“RemediationStrings”:[{“Language”:”en_us”,“Title”:”Defder Antivirus Should be activate”,“Description”:”Defender Antivirus Should be Activate”}]},{“SettingName”:”DefenderVersion”,“Operator”:”GreaterEquals”,“DataType”:”Version”,“Operand”:”4.18″,“MoreInfoUrl”:”https://learn.microsoft.com/en-us/mem/intune/protect/device-compliance-get-started”,“RemediationStrings”:[{“Language”:”en_us”,“Title”: “Defder Antivirus Should be activate”,“Description”: “Defender Antivirus Should be Activate”}]},{“SettingName”:”DefenderServiceStatus”,“Operator”:”IsEquals”,“DataType”:”Boolean”,“Operand”:”True”,“MoreInfoUrl”:”https://learn.microsoft.com/en-us/mem/intune/protect/device-compliance-get-started”,“RemediationStrings”:[{“Language”:”en_us”,“Title”: “Defder Antivirus Should be activate”,“Description”: “Defender Antivirus Should be Activate”}]},{“SettingName”:”SigStatus”,“Operator”:”LessEquals”,“DataType”:”Int64″,“Operand”:”14″,“MoreInfoUrl”:”https://learn.microsoft.com/en-us/mem/intune/protect/device-compliance-get-started”,“RemediationStrings”:[{“Language”:”en_us”,“Title”: “Defder Antivirus Should be activate”,“Description”: “Defender Antivirus Should be Activate”}]},{“SettingName”:”OSVersion”,“Operator”:”GreaterEquals”,“DataType”:”Version”,“Operand”:”10.0″,“MoreInfoUrl”:”https://learn.microsoft.com/en-us/mem/intune/protect/device-compliance-get-started”,“RemediationStrings”:[{“Language”:”en_us”,“Title”: “Defder Antivirus Should be activate”,“Description”: “Defender Antivirus Should be Activate”}]}]}
Now open Intune Console and go to Devices and then Compliance Policy.
Under Compliance Policy Click on Scripts.
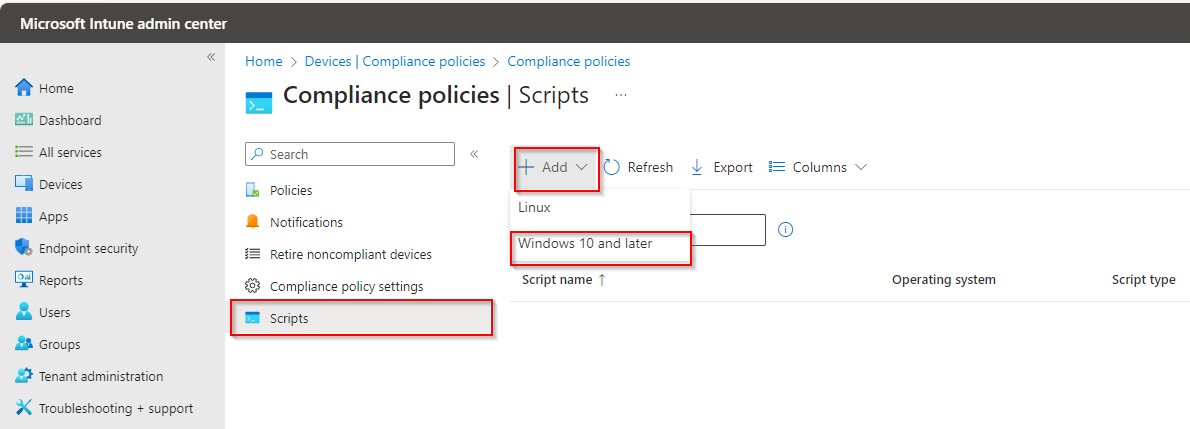
Fill the script name.
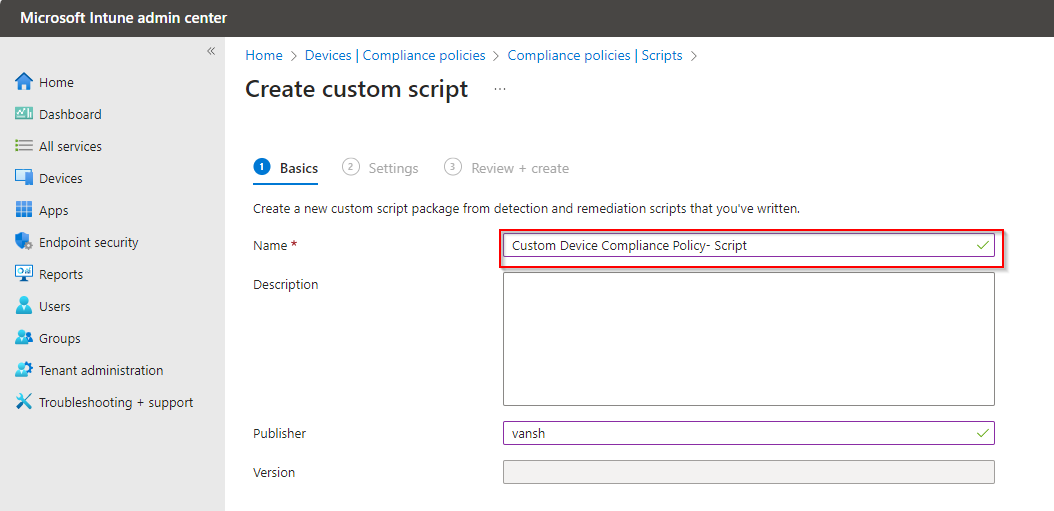
Past your PowerShell script here.
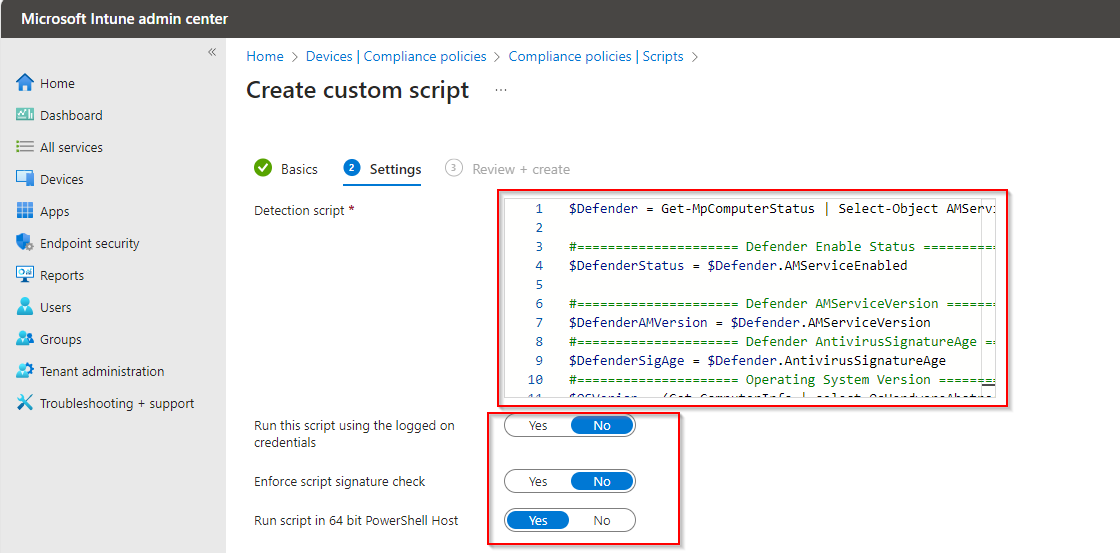
Click on Next after past the script.
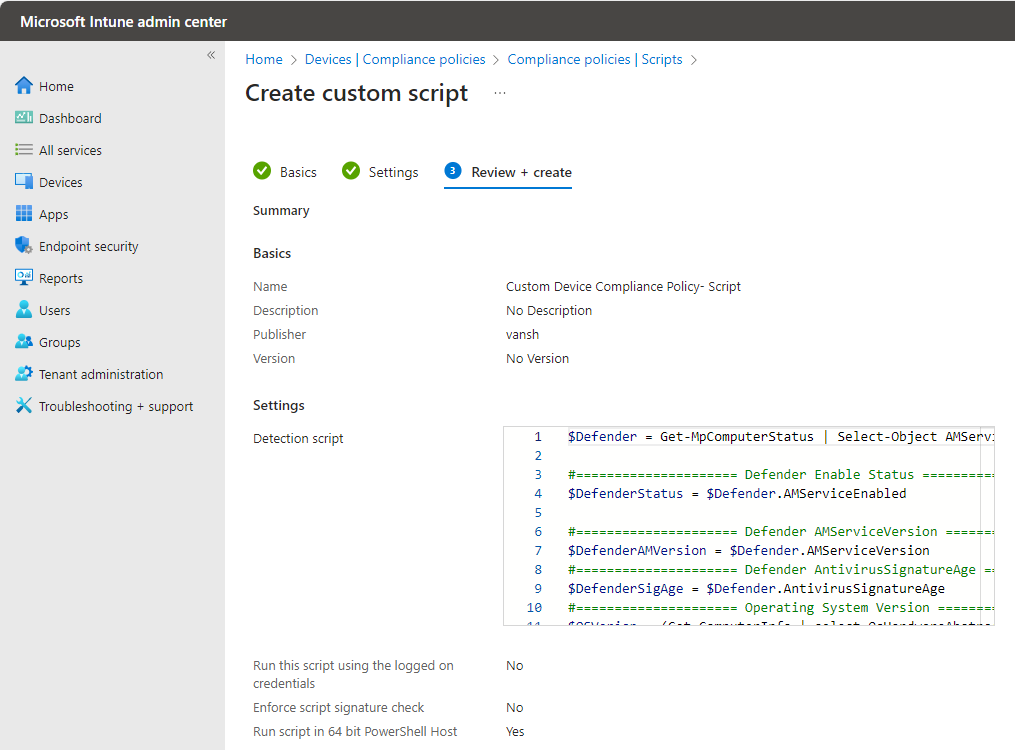
Here is script create.
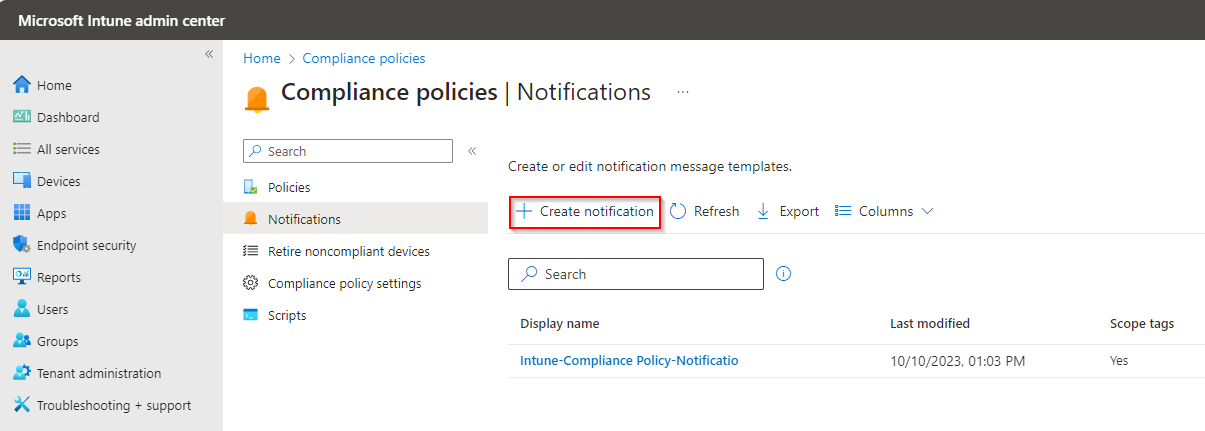
Now Select the Notification and fill the Notification Name.
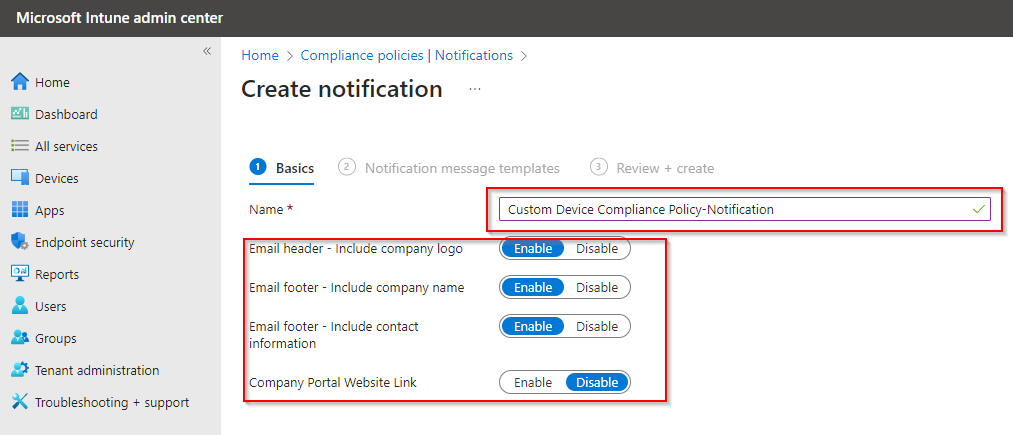
Click on Next and fill the notification details here.
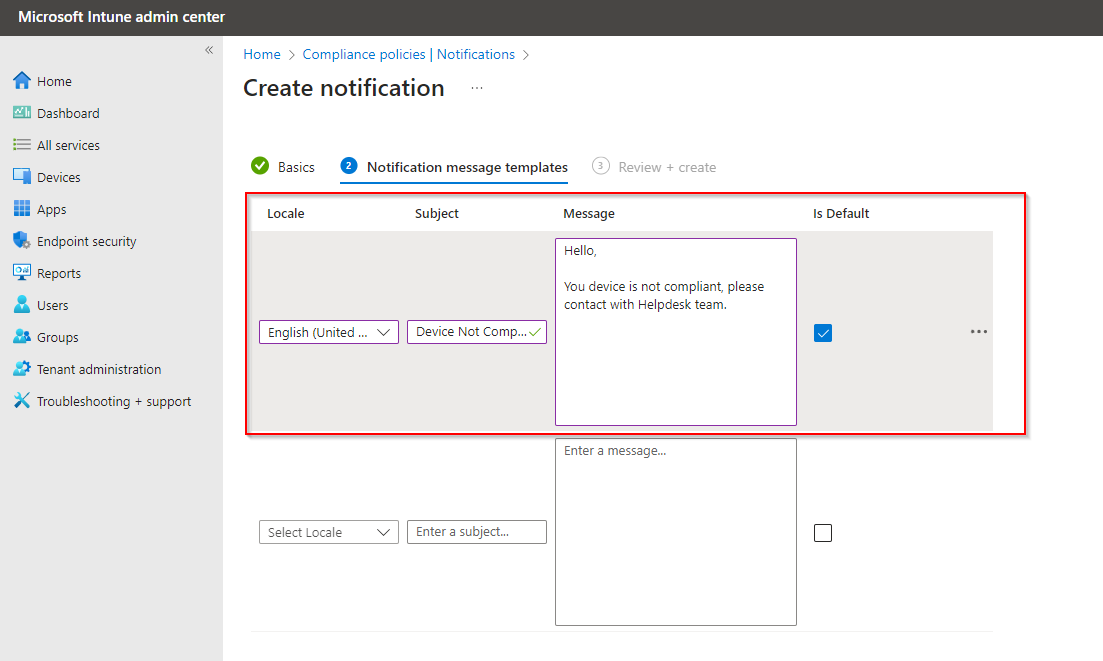
Now click on Create to setup your notification.
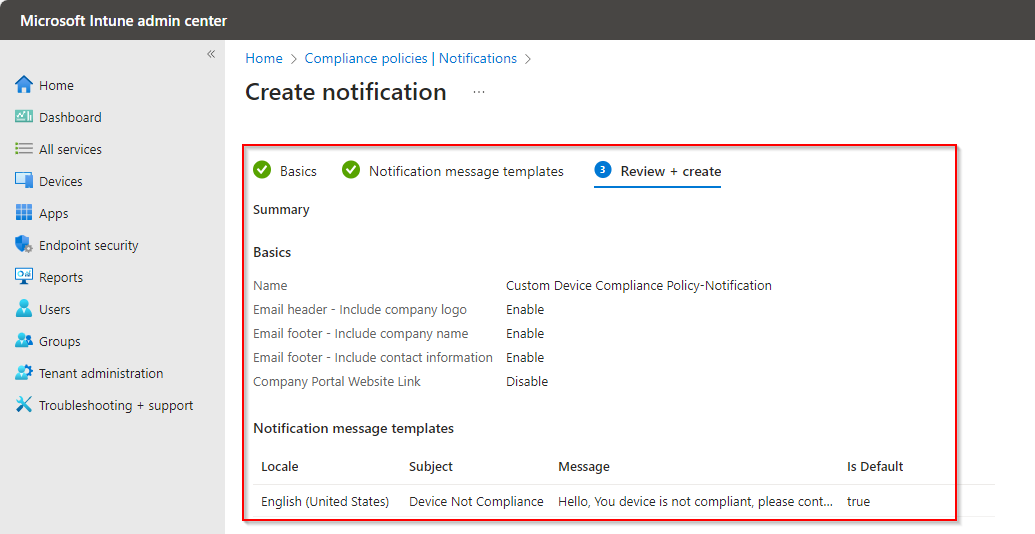
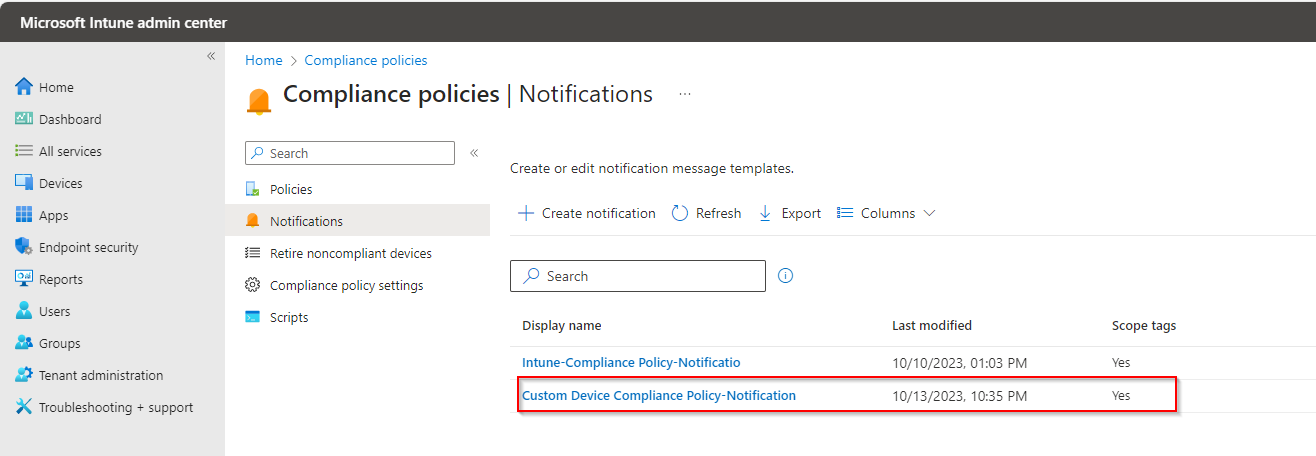
Here you is your Notification.
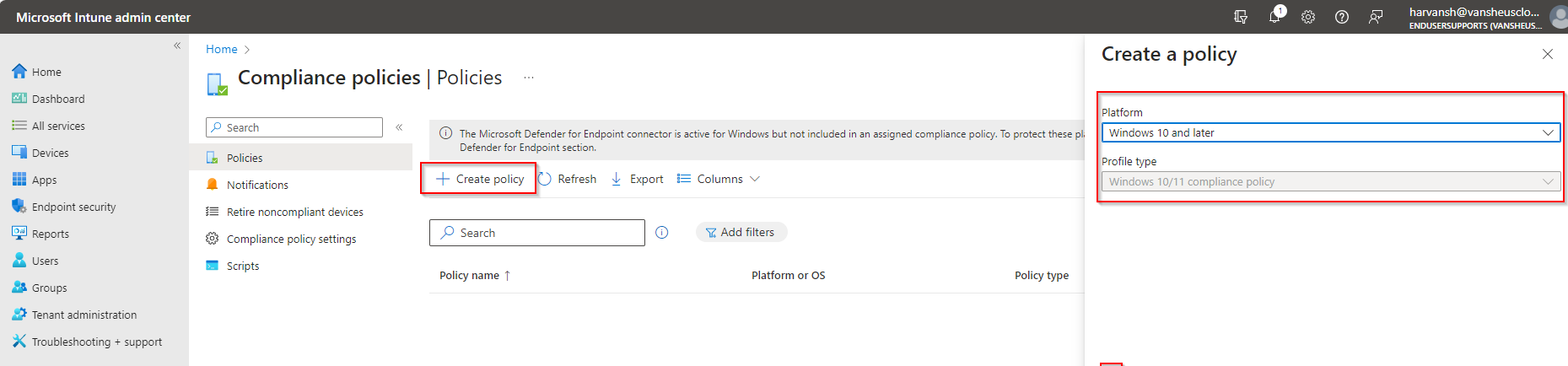
Now click on Policies and click on Create Policy. Select Window 10 and Later then click on Create.
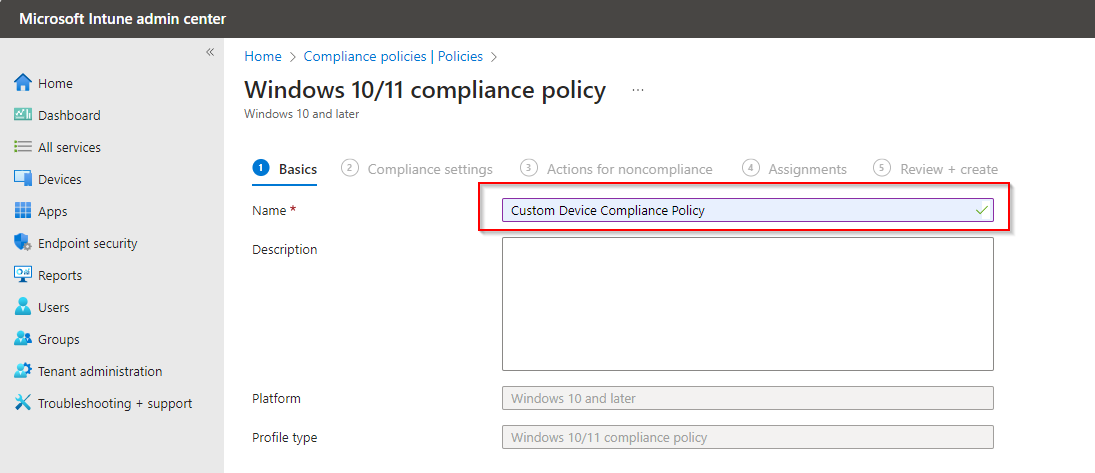
Fill the Policy name here.
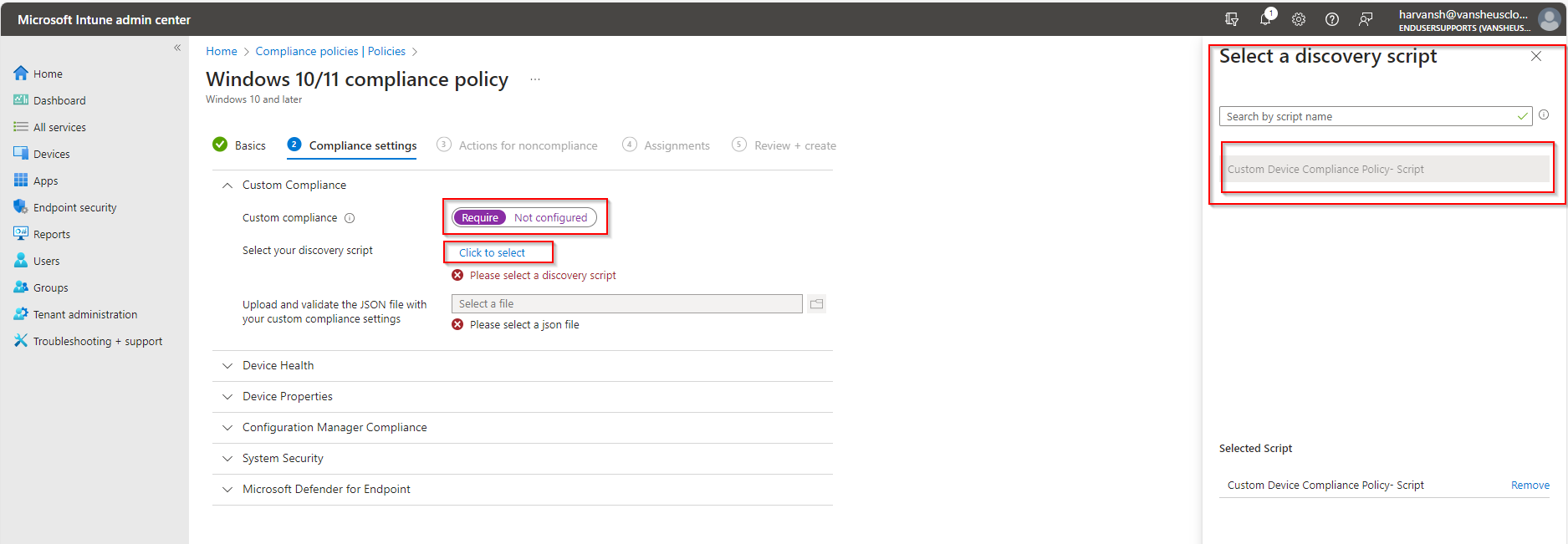
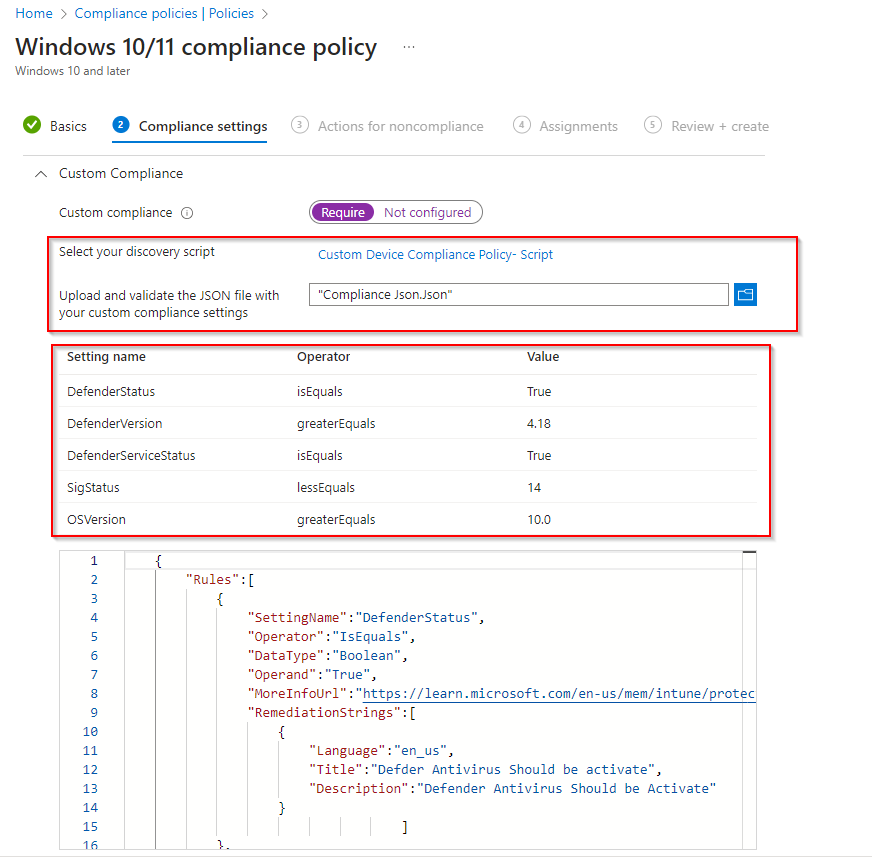
Click on Custom Compliance settings and select Required option. Then click on select your discovery script. Now select the script we created.
Now Browse the Jason file you downloaded from Github or copy from from the blogs. Click on Next. Below screen will shows error if any issue with the JSON.
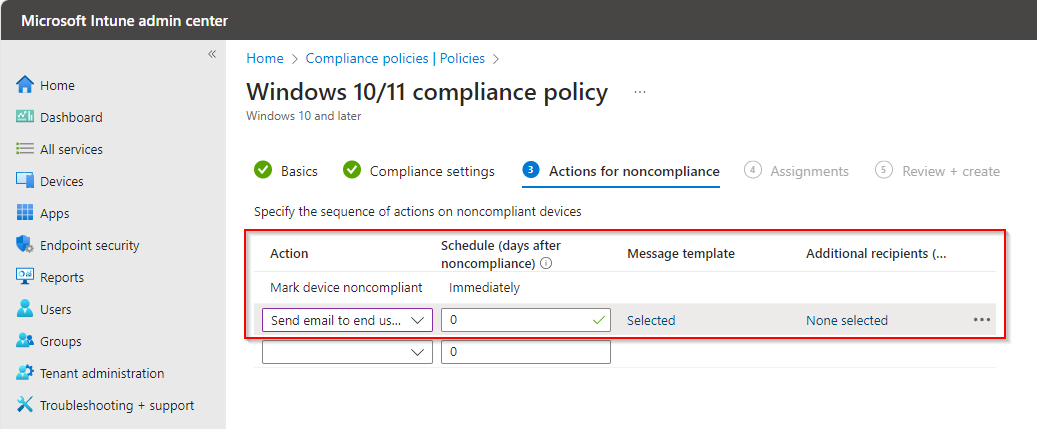
Now select the Notification we created.
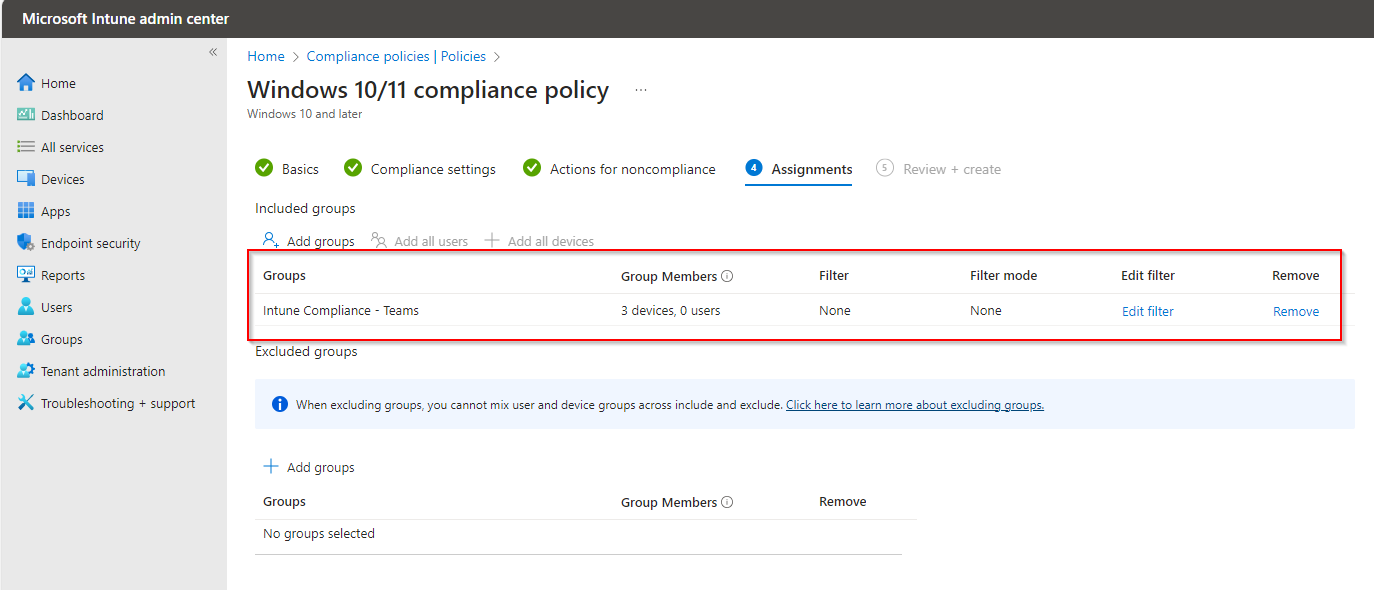
Now select the group name to deploy the script.
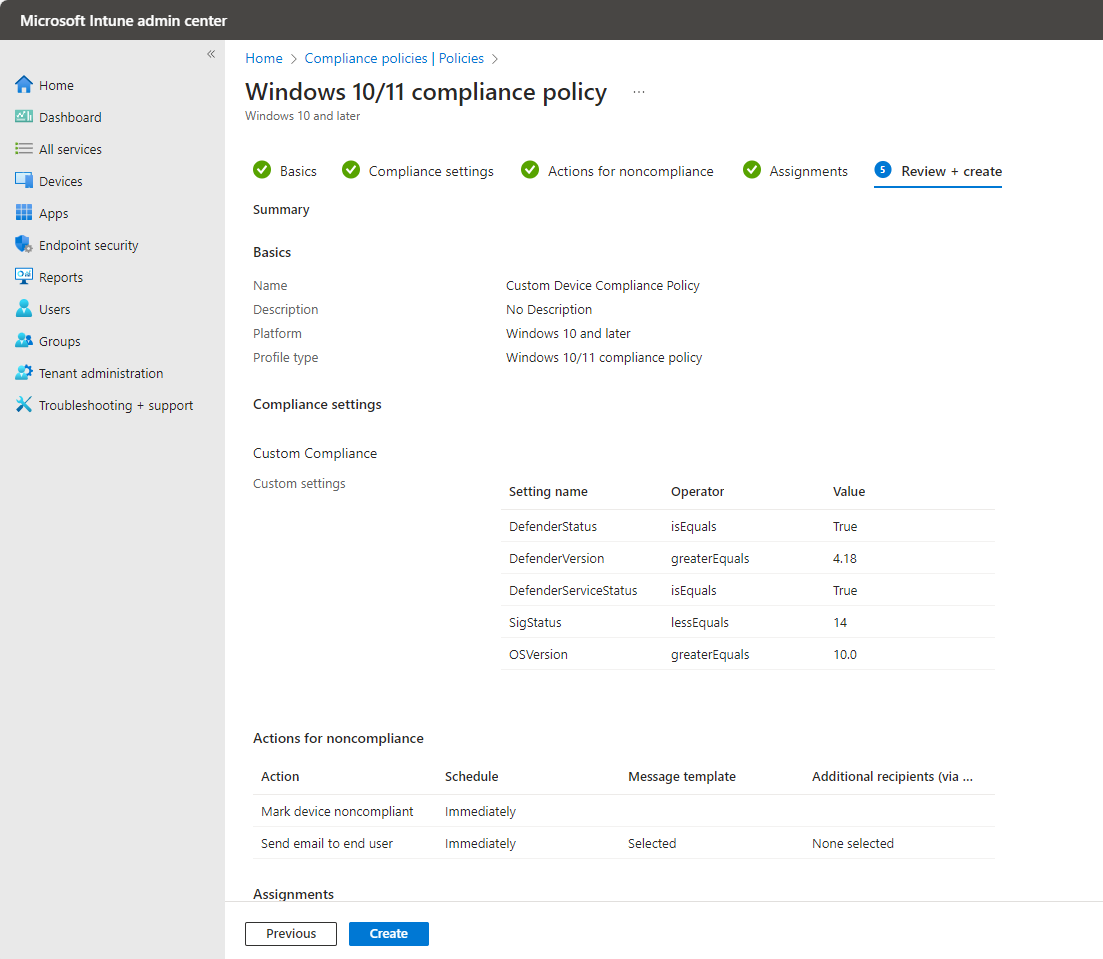
Finally we created the script and deployed.
Wait for couple of hour to update the policy on User device. Open again Policy and see the status as below.
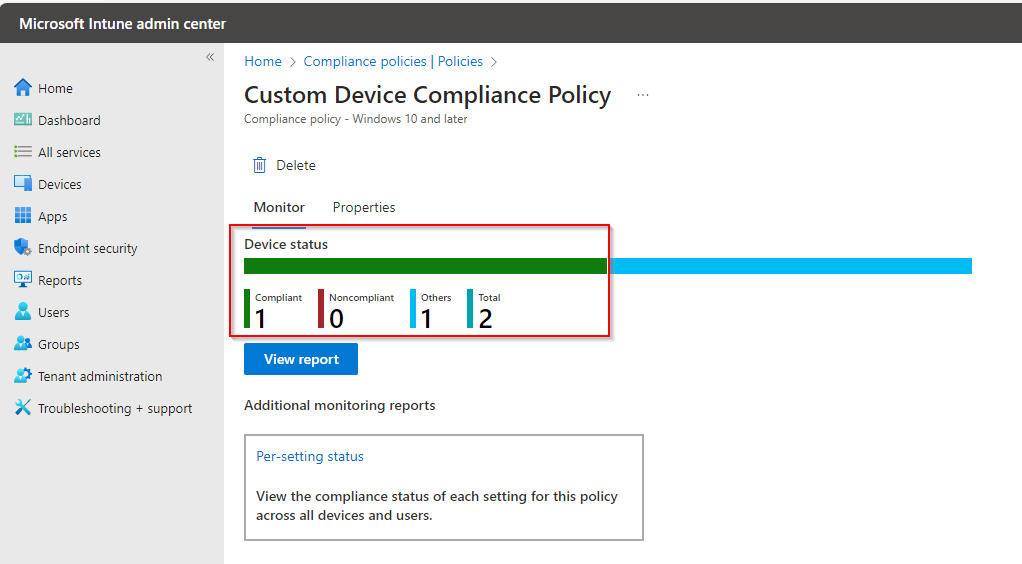
For more investigation, Go to the devices and and search any device name and then open it. Now click on Compliance Policy tab to check the compliance policy status for that device.
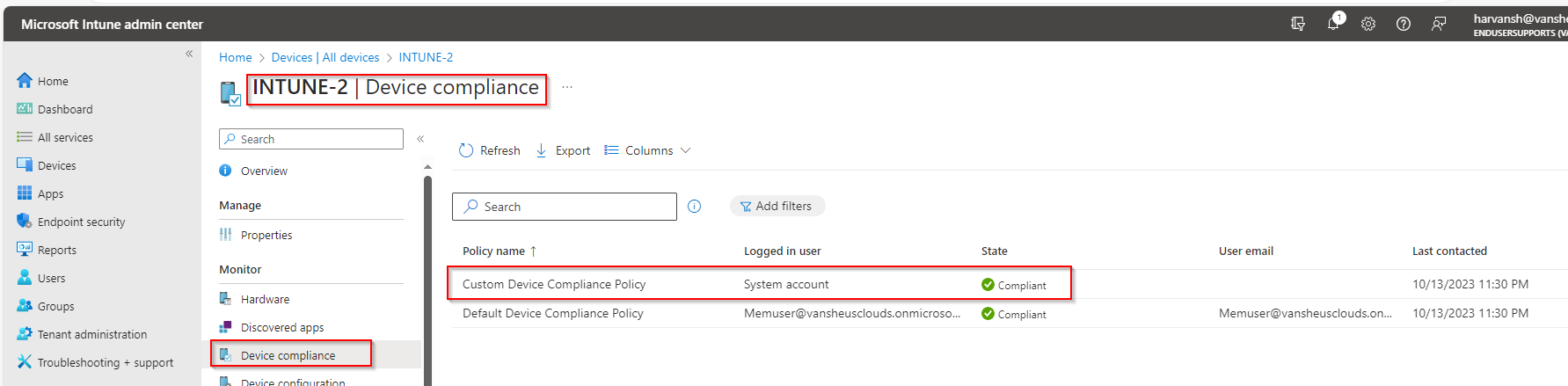
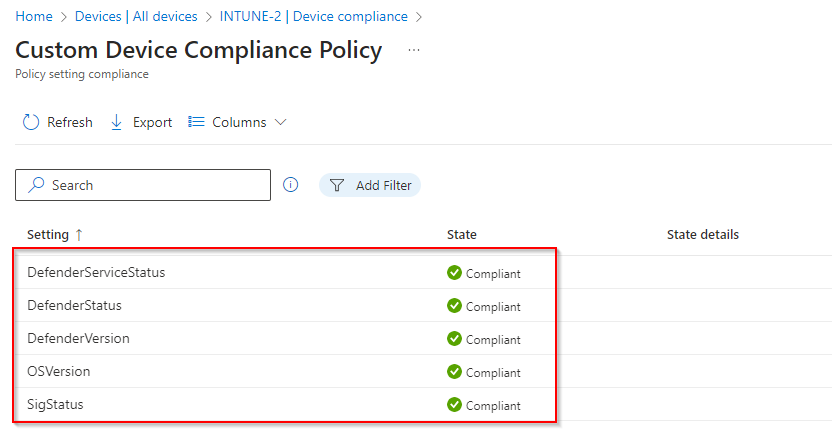
Now click on the Compliance policy to check the details.
Here is the video for Custom Device Compliance.

[…] Custom Device Compliance Policy in Intune […]