Proactive Remediation in Intune
- Remediation script will hep you to detect the issue on user device before they realize they have issue on their Device.
- Remediation script will detect and fix the issues.
- You can create your own script for Detection and Remediation on PowerShell.
- Each script package consists of a detection script, a remediation script, and metadata
Prerequisites
Whether enrolling devices via Intune or Configuration Manager, Remediation scripting has the following requirements:
Devices must be Microsoft Entra joined or Microsoft Entra hybrid joined and meet one of the following conditions:
- Is managed by Intune and runs an Enterprise, Professional, or Education edition of Windows 10 or later.
- A co-managed device running Windows 10, version 1903 or later. Co-managed devices on preceding versions of Windows 10 will need the Client apps workload pointed to Intune (only applicable up to version 1607).
Licensing and Permissions requirement
Remediation requires users of the devices to have one of the following licenses:
- Windows 10/11 Enterprise E3 or E5 (included in Microsoft 365 F3, E3, or E5)
- Windows 10/11 Education A3 or A5 (included in Microsoft 365 A3 or A5)
- Windows 10/11 Virtual Desktop Access (VDA) per user
You should have Intune Administrator or Global Administrator access
Script requirements
- You can have up to 200 script packages.
- A remediation script only runs if the detection script uses exit code exit 1, meaning the issue was detected.
- If the option Enforce script signature check is enabled in the Settings page of creating a script package, then make sure that the scripts are encoded in UTF-8 not UTF-8 BOM.
- The maximum allowed output size limit is 2048 characters.
- Don’t put reboot commands in detection or remediation scripts.
- Do not include any type of sensitive information in scripts (such as passwords)
- Do not include Personally Identifiable Information (PII) in scripts
- Do not use scripts to collect PII from devices.
Detection Script
# Script to check Defender Antivirus Definition
$Days = 10
$Defage = (Get-MPComputerStatus).AntispywareSignatureAge
if ($Defage -le $Days)
{“Compliant”}
Exit 0
Else {
“Non-Compliant”
}
Exit 1
Remediation Script
# Script will update Defender Anntivirus Definition
$Days = 10
$Defage = (Get-MPComputerStatus).AntispywareSignatureAge
Try {
Update-MpSignature
if ($Defage -le $Days)
{“Compliant”}
exit 0
Else {
“Non-Compliant”
exit 1
}
}
Catch
{
“Definition update failed”
}
Exit 0
Login to Intune Console and click on Devices.

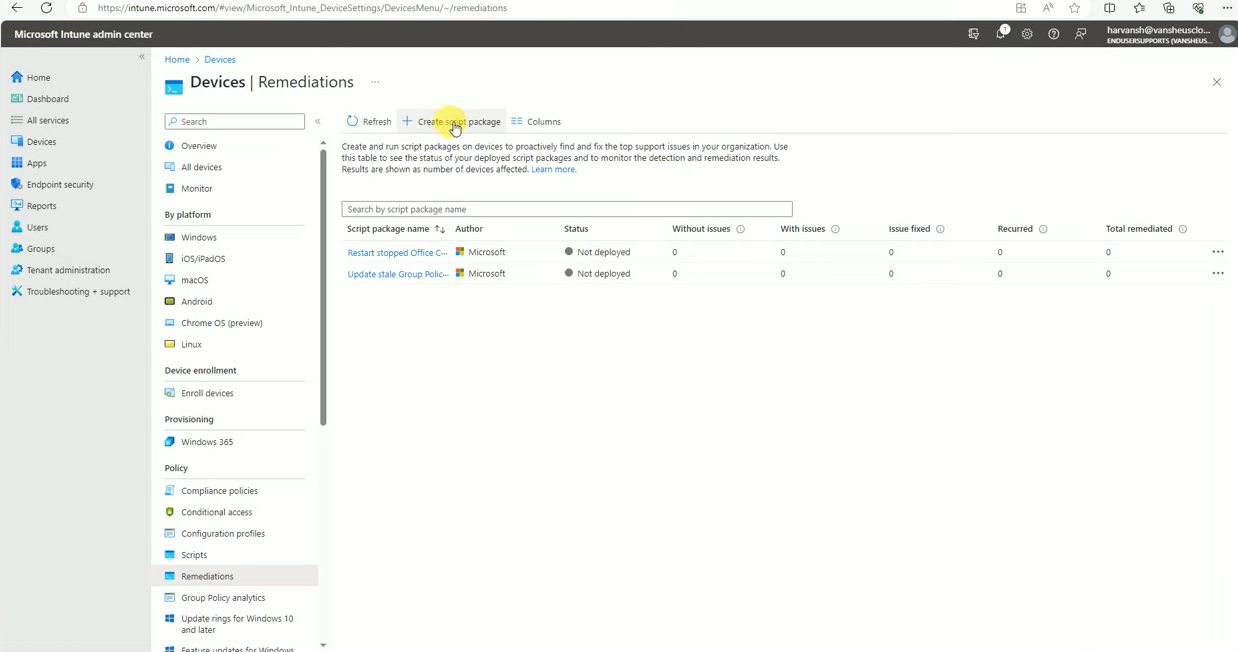
Click on Remediation option and click on Create Package.
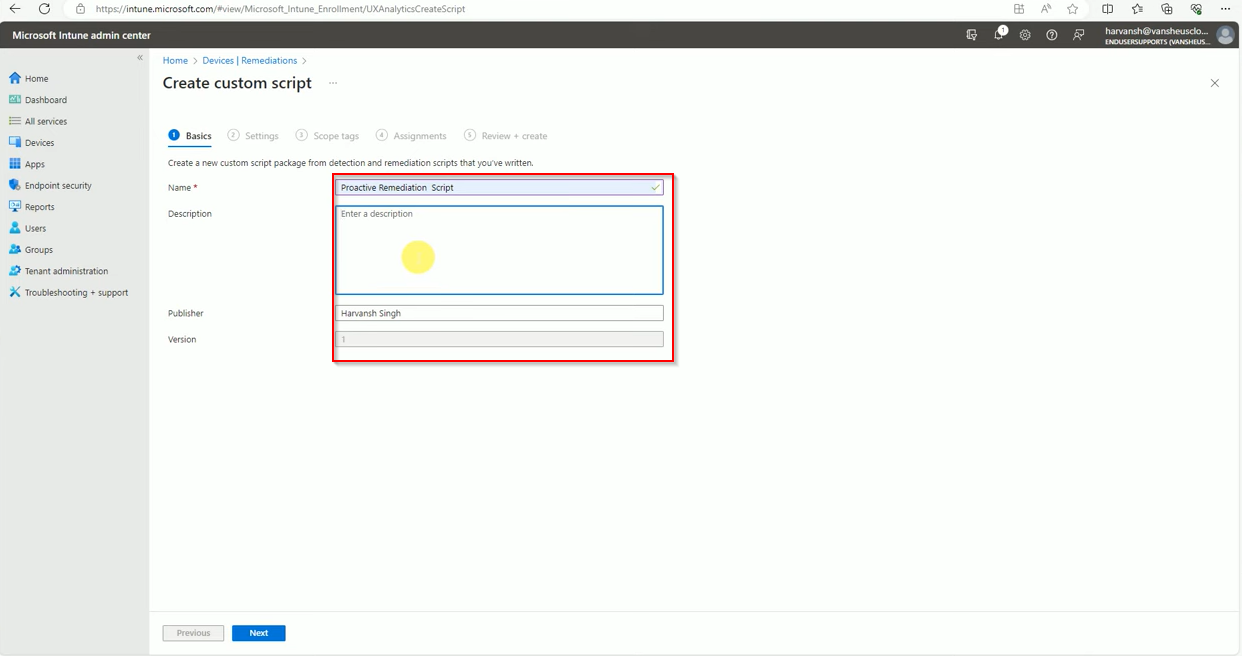
Fill the details and click on next.
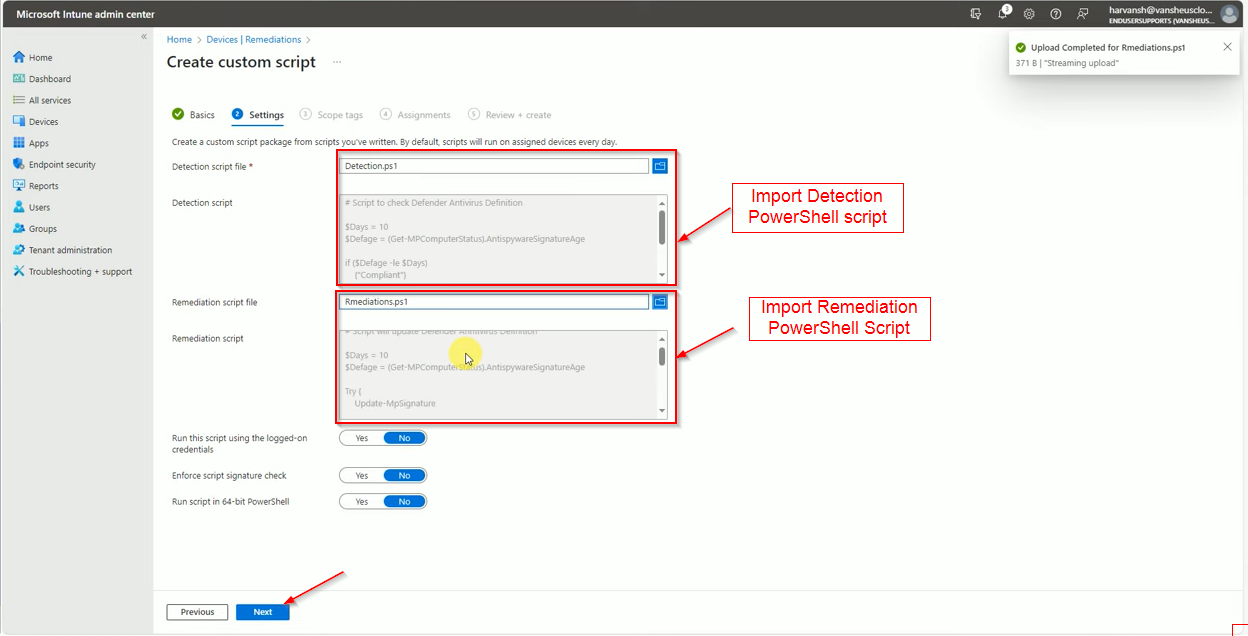
Import PowerShell Script for Detection and Remediation then click on Next.
Add the scope if needed, its not a mandatory to add scope.

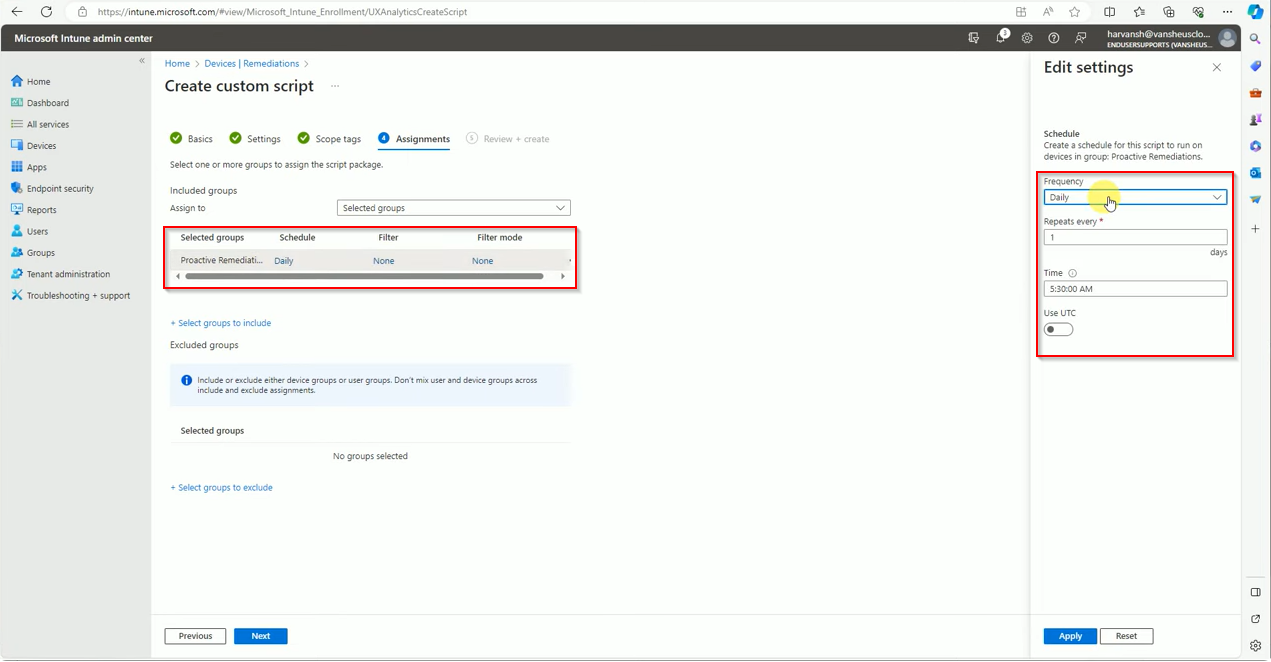
Now assign the group name where you want to deploy the Remediation script.
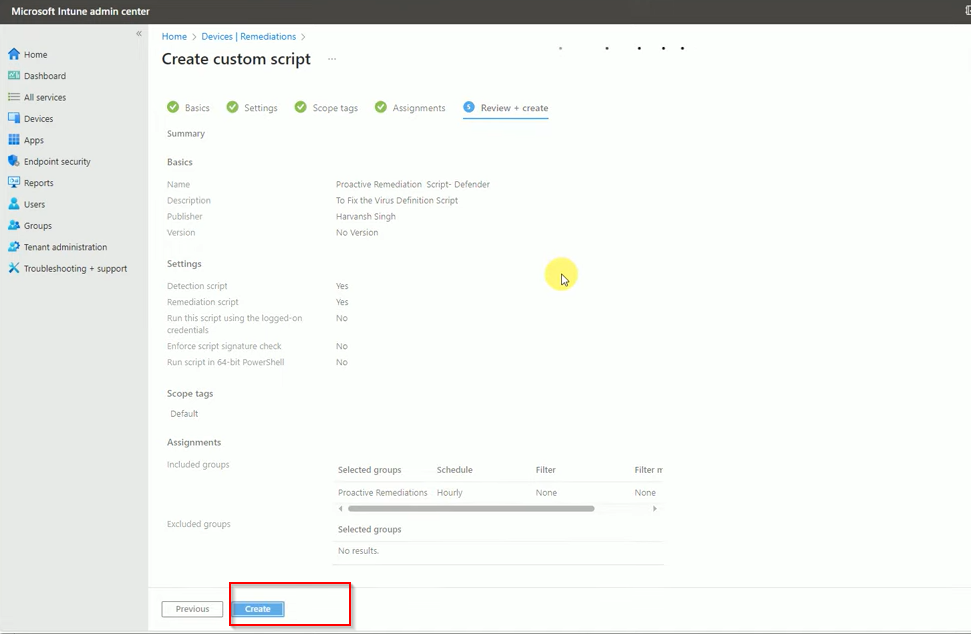
Finally review the policy and click on Create button.
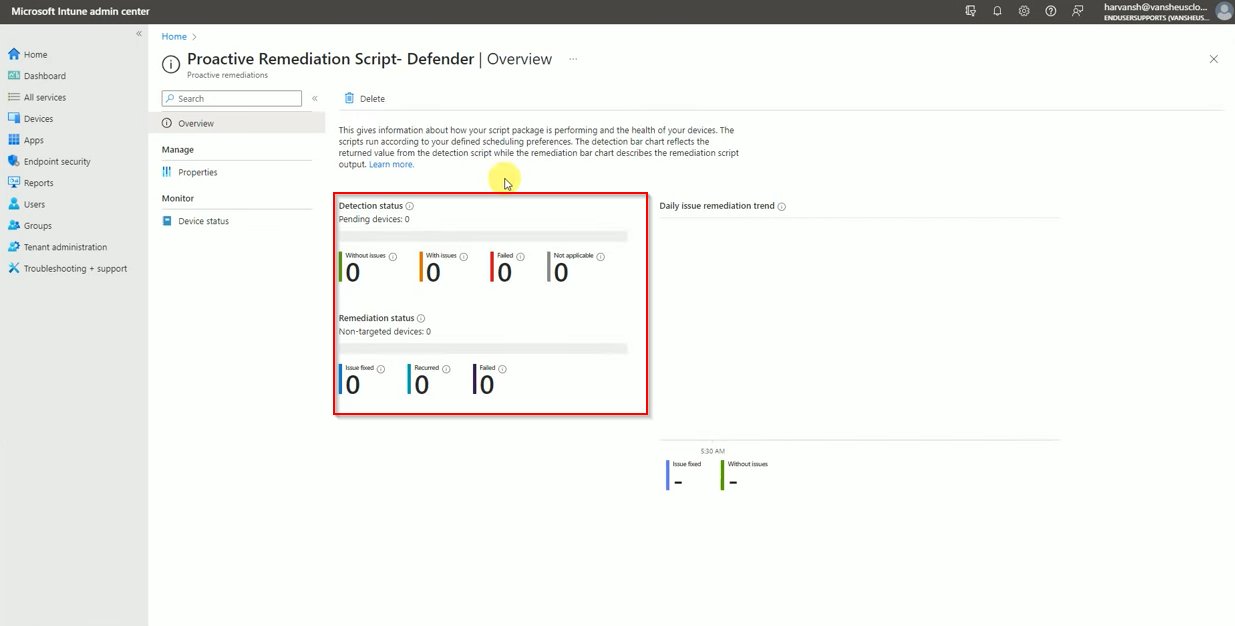
After Deployment, you can see the result here.